August 9, 2018
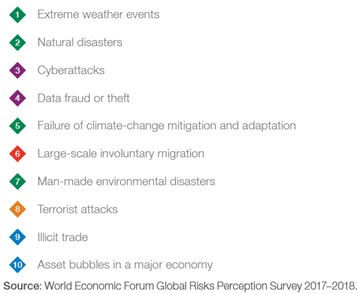
In January 2018, The World Economic Forum published its Global Risks Report, finding that in terms of likelihood,Cyberattacks and Data Fraud or Theft fell 3rd and 4th in international risks facing businesses, both rating at around 4 out of 5 in corporate risk levels. Extreme Weather Events and Natural Disasters were the only two ahead on the list, but unlike environmental risks, technological ones can practically be managed and mitigated.
The latest gold mine for hackers.
The legal industry has particularly seen a stark increase in data breaches as cybercriminals realize the value of information they can tap into and how easy it often is to access. The industry has even been labeled “the latest gold mine for hackers.”
This is because of the value of information circulated in the legal industry, and the easy access to client networks through firm networks. This can prove to be extremely damaging and the financial impact can compound into hundreds of millions of dollars, taking into account equipment replacement, regulatory fines, and lost business among other consequences.
Third party involvement in a breach increases the cost.
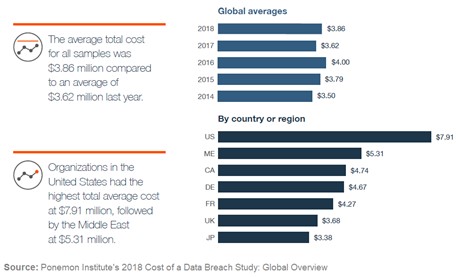
The Ponemon Institute's annual Cost of a Data Breach Study reported earlier this month that on average, the cost of a breach of at least 1,000 lost or stolen records rose a quarter of a million dollars, from $3.62M to $3.86M. Third party involvement in a breach increases the cost. If a third party caused the data breach, the cost increased by more than $13 per compromised record for an adjusted average cost of $161, up from $148 per record.
Very few organizations can handle such costs, with major data breaches estimated to have average costs of $39 million -$350 million depending on the amount of data breached and the rate at which it was contained. For smaller organizations, a data breach can easily put them out of business.
Devastating consequences.
Let’s look at two examples of data breaches that had devastating consequences:
In 2010, hackers instigated a massive attack on Canadian law firms, companies, and the government, successfully penetrating at least seven firms, including prominent firms Stikeman Elliot and Blake, Cassels & Graydon, in search of exclusive information on a takeover of the Potash Corporation. Daniel Tobok, who investigated these wide-spread attacks, stated that the attack was not only “very sophisticated and highly targeted” but that “nobody knew the severity of the issue or what was happening.” Not only were companies and firms targeted, but the cyber attack’s success in penetrating the Canadian government’s computers shut down all internet connections to the Finance Dept and Treasury Board and divisions of the Dept of National Defense, and almost a year later, all three departments still didn’t have full internet access. The consequent shut down of the deal cost nearly $40 Billion in the loss of the deal alone, with millions more in lost business and data.
Even more infamous was the attack on Mossack Fonseca, the fourth largest offshore law firm, when more than 2.6 terabytes of information was stolen and nearly 11.5 million documents were leaked. An estimated $135 billion was wiped off of the value of nearly 400 companies after what was dubbed The Panama Papers incident, not to mention the massive fines and closures the firm faced. The information leaked led to numerous investigations, high-profile resignations, police raids and arrests, protests, and national legal reforms, amongst other consequences. According to Hannes Wagner of Milan’s Bocconi University, the financial hits to companies following the Panama Papers represents “the largest [overall] loss in history” following a data breach.
Too many organizations are still employing a reactive stance than a proactive one.
Despite more awareness of the prevalence and reality of attacks, too many organizations are still employing a reactive stance than a proactive one. For law departments and firms especially, it is too little, too late to ask for security certifications from technology vendors when a breach has already taken place. Cybersecurity consideration and preparedness must be sought and enforced from the onset, built into law department and firm technology acquisition processes and centralized in the same way other vendors due diligence processes are performed.
Use ISO 27001 Certified, fully secure Counself Risk platform to send Due Diligence Requests to your vendors, create and circulate intelligent Forms that streamline the data collection process for you and your vendors, and maintain full audit histories and access security restrictions for ease of monitoring and maintenance. Please contact us here for more information.